It’s really difficult for the people to upgrade the current ADFS infrastructure to the latest one when old one is out of support.
what ADFS is and why it’s used in any organization:
Active Directory Federation Services (AD FS) is the claim-based single sign-on (SSO) solution provided by Microsoft. It facilitates access to all integrated applications and systems with just your Active Directory (AD) credentials.
Authentication flow:
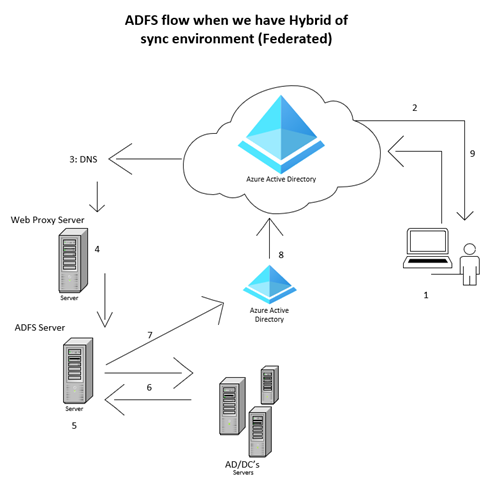
1: User opens Office365/Microsoft login page and type in the Login ID and hit enter
2: Login Query reaches to AAD and found the domain is Federated and redirect to ADFS page to enter the password.
As soon as user enter password the token will try to get the authentication confirm and follow the configuration. As per the configuration the query will reach to DNS.
3: DNS should have A Record pointing to FQDN to Resolve Query to Proxy server for the next step.
4: Proxy server will cross check internally and accept the query if it’s for legit user and hand over to ADFS to check. To hand over the query, need to create A record on DNS server to communicate from Proxy to ADFS.
5: Now ADFS will send the LDAP query to AD for the user validation and if AD account found then.
6: AD/DC will revert with an Authorized token.
7: ADFS will relay the Authorized Token to AAD connect.
8: Now AAD connect agent will relay the Authorization to AAD
9: AAD connect will allow the user login to access the Authorized resources.
How can you configure all this?
Requirements:
1 ADFS server
1 Web Proxy server (Load Balance) it should be in Perimeter (Edge/DMZ) for extra security.
1 Valid SSL certificate
Note: Always recommended to have 2 ADFS and 2 web proxy for backup/fallback scenario if 1 down.
Installation guide for ADFS server:
Open Server Manager > Click on Manage > Add roles > and follow the below screenshots:
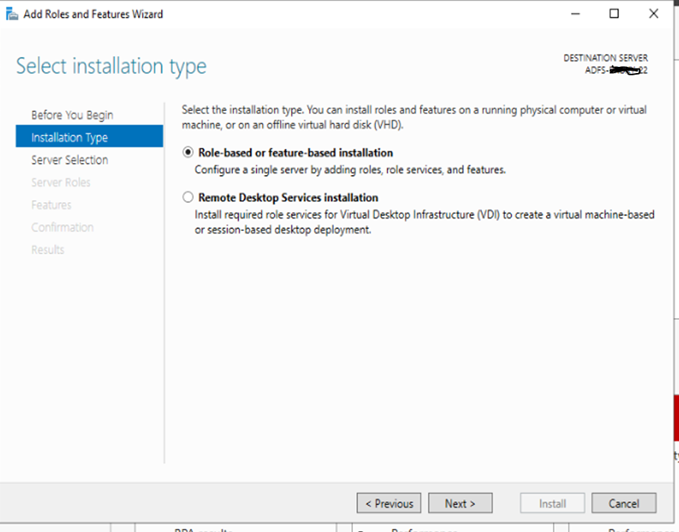
a: Select Role based or feature based installation and click next
b: Select the destination server on which you want to install the role:

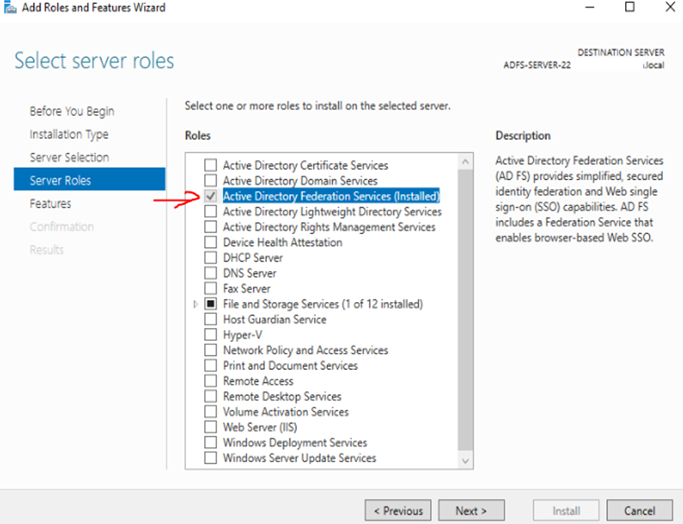
c: Select ADFS role and click next:
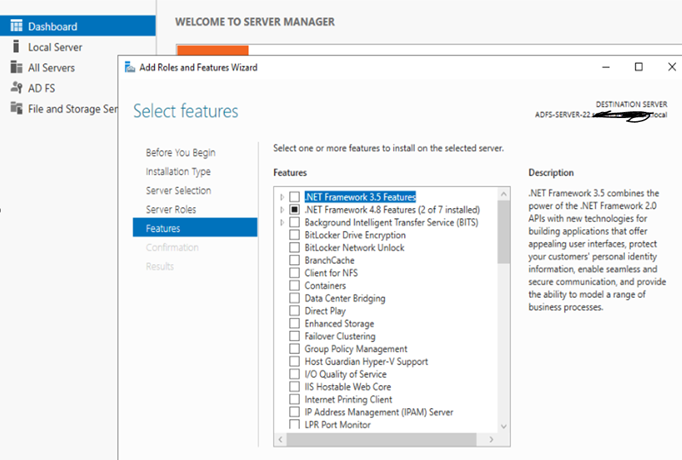
d: Select option featured if any requirement to install, mandatory once already selected:
e: If you already have ADFS environment which is in running situation or supported version. Then you can select the option to add a server to a federation server Farm.
We going to select Create as old environment is not supported in our scenario or we are upgrading from old to new:
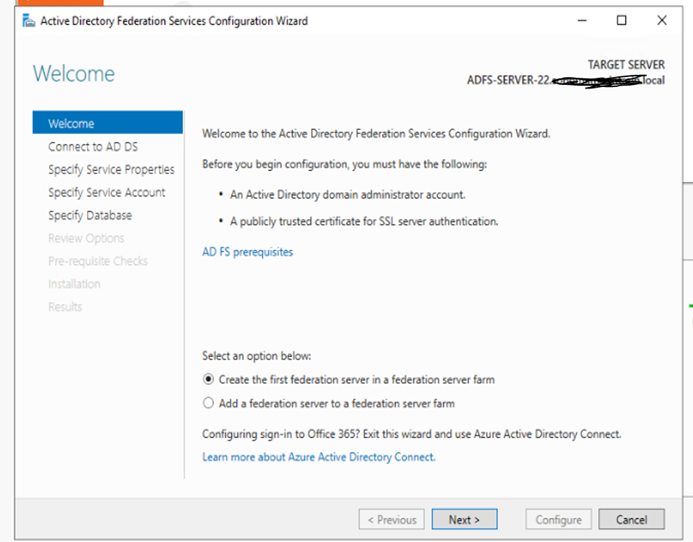
f: Click next and it will ask to install. After installation you will see the option to configure
ADFS on the same window.
Use the Enterprise Admin Account to configure it.
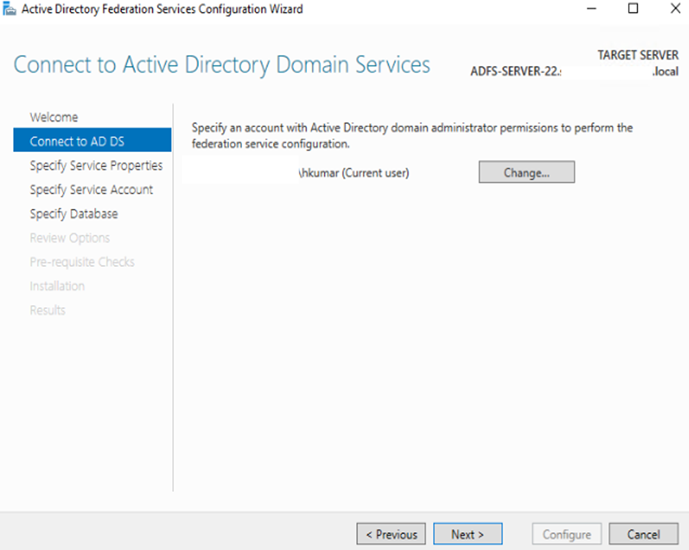
g: enter the Enterprise Admin cred. to configure or if you want to create a service account for it if you haven’t then selectedthe option to create.
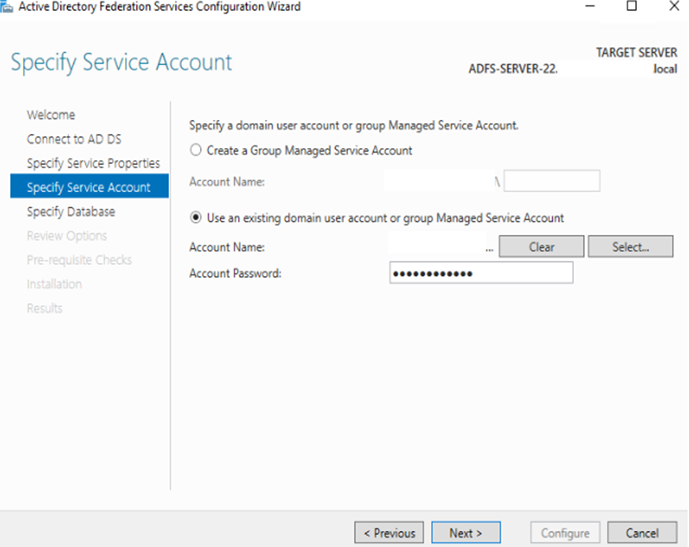
h: If your organization is using SQL database then use the same database. If not then proceed to create windows data base.
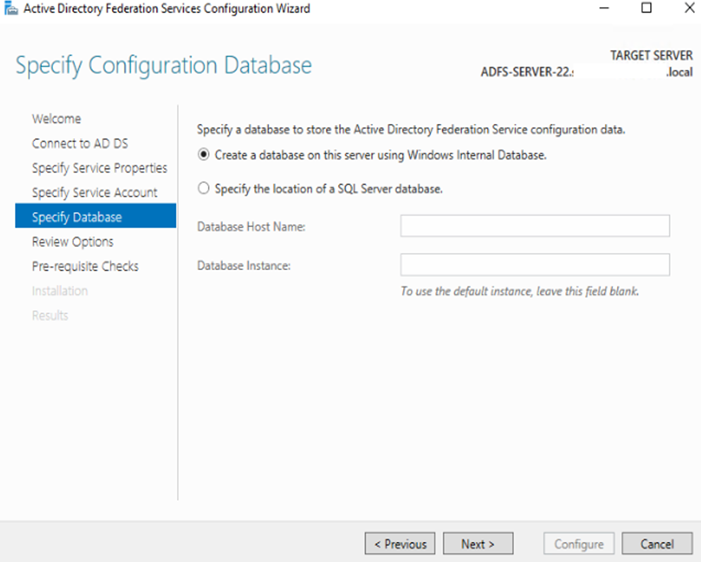
i: Review and click next to configure things:
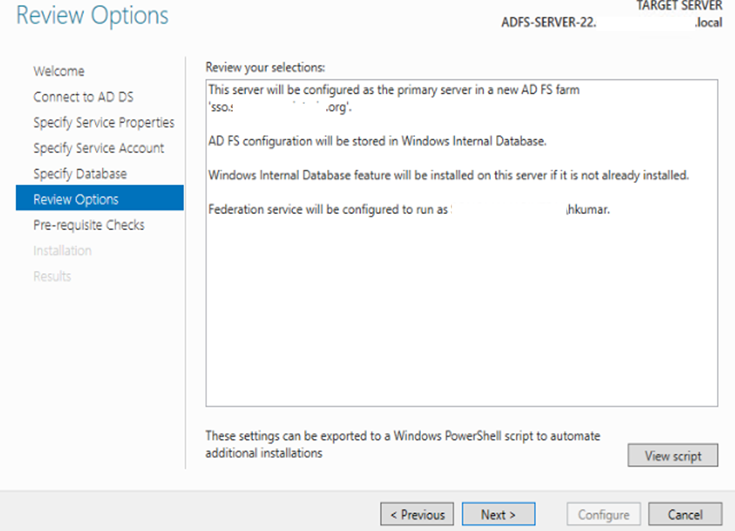
j: Click configure to deploy once deployed it will give you some warning (which you can ignore).
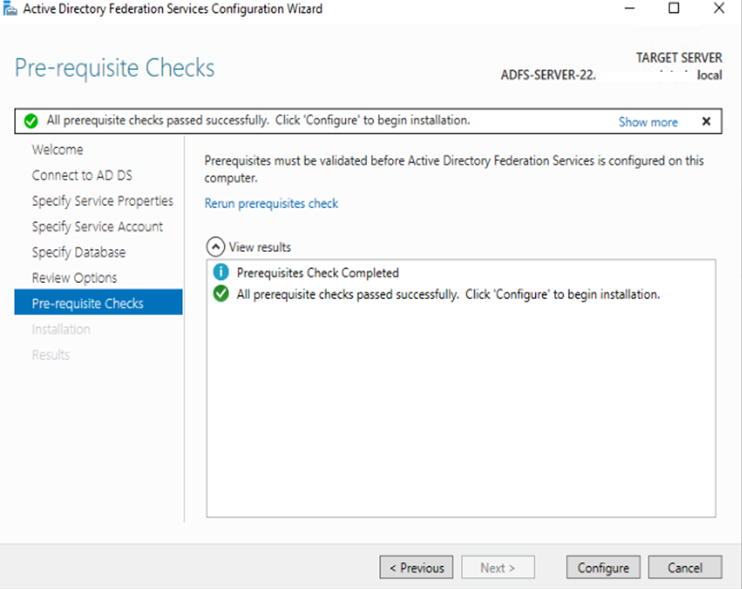
h: You can ignore these warning as its just requirements which you need to confirm if not in place.
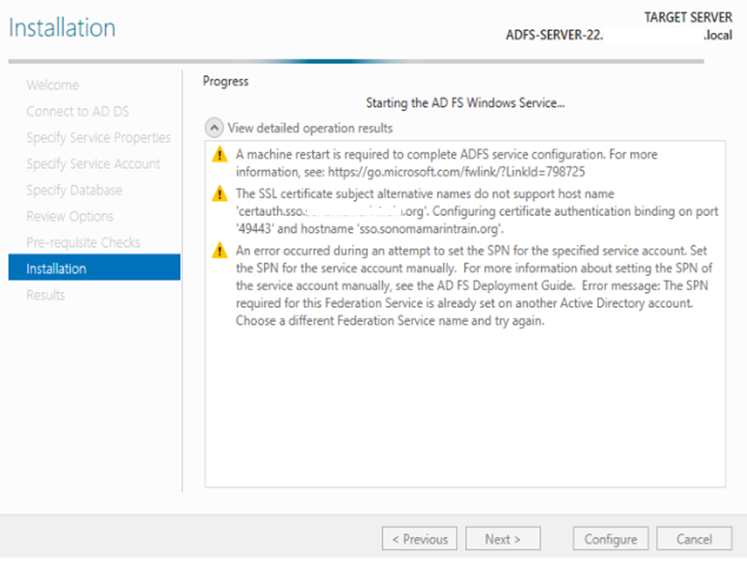
Now we need to register the ADFS server for Authentication, this will be configure using PowerShell:
Open PowerShell on ADFS server and run the below PS cmd:
Initialize-ADDeviceregisteration -serveraccountname domain.com\username.
Now you will be prompted to enter the credentials. If everything good then you will see the below kind of screen.
Now you need to stamp the certificate. Make sure it is installed on the Machine already. If not, then do it before proceeding to next.
Add-AdfsCertificate -CertificateType “Token-Signing” -Thumbprint “Enter the Certificate thumbprint value”
Set-AdfsCertificate -IsPrimary -CertificateType “Token-Signing” -Thumbprint “Enter the Certificate thumbprint value”
Now need to enable the endpoint:
Enable-ADFSendpoint -TargetAddress /adfs/services/trust/13/windows (This is to enable the endpoint)
Set-ADFSendpoint -TargetAddress /adfs/services/trust/13/windows -proxy $true (This is require to enable to communicate to proxy server)
Set-ADFSproperties -nettcpport 809 (This port is require to open to communicate on ADFS)

How to install Proxy server and configure:
1: Go to Server Manager and add role:

2: Select Role based or feature based installation and then Click Next:

3: Select the server to install the roles and then click next to proceed:

4: Select the roles and then click next to proceed:
5: Select the extra features to add and then click next to proceed:
6:
7: Click on add features and these will be add to install:
8: Click on install to proceed:
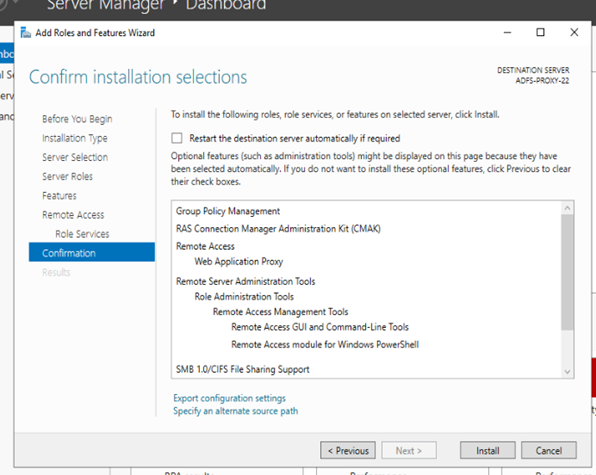
After installation, please restart the Proxy server and ADFS both.
Install the SSL certificate on web proxy server as well.
Now you require to configure the web proxy server to work well with ADFS:

On the next screen, you require to select the certificate you installed:
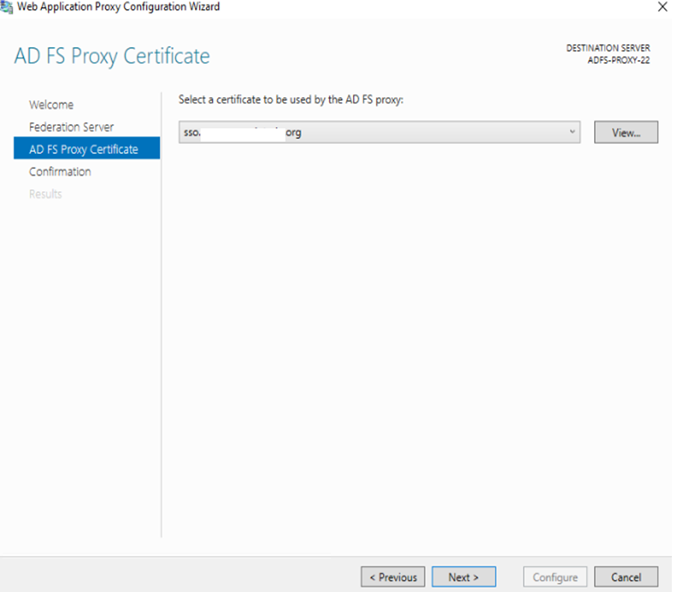
Now on this screen it will check and try to communicate to ADFS if all good then this will be configured well.
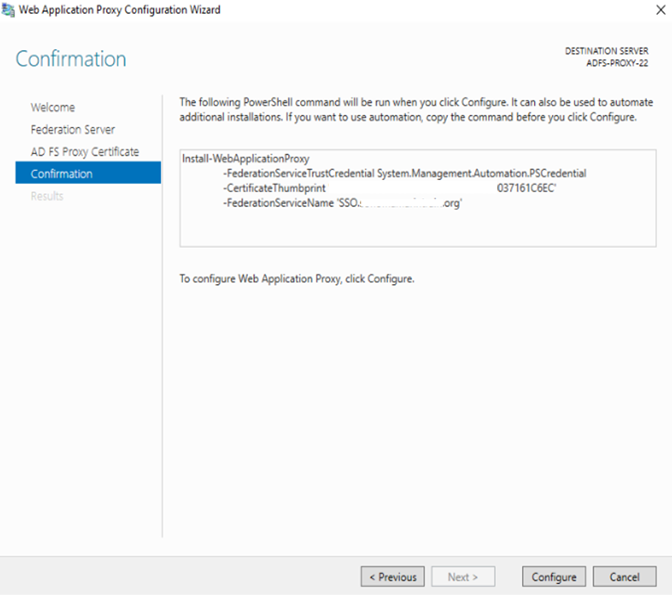
Make sure you have updated the ADFS context to MSOL/Azure active directory, if not below is the PS cmd to it:
Connect to MSOL Service PowerShell to run:
- Update-MSOLFederatedDomain –DomainName Domain.com
- Set-MSOLAdfscontext ADFS-server-22
Thank you for reading this, BLOG.
HARISH KUMAR