Cloud PCs are a powerful tool in modern enterprise environments, enabling flexible, secure access to Windows desktops from virtually anywhere. However, when authentication issues occur—especially during login via the Windows Remote Desktop app—it can stall productivity and confuse users.
Recently, we encountered a Cloud PC login issue where the user was unable to sign in through the Windows app, receiving a generic “Login Failed” error message. Here’s a breakdown of the troubleshooting process and the successful resolution.
Issue Summary
- Symptom: Login failed when accessing Cloud PC via the Windows Remote Desktop app.
- Platform: Microsoft Entra ID-joined Cloud PC.
- Observation: No sign-in logs were generated in Azure AD or Intune, indicating the issue was occurring before authentication could complete.
Troubleshooting Steps Performed
- Re-installed the Windows Remote Desktop app
- To rule out corruption or configuration issues in the local RDP client.
- Checked Azure Sign-In Logs
- No failed login attempts were found, pointing to a local configuration or policy issue.
- Reviewed Local Security Configuration
- Inspected the local security policies and registry values that might affect online ID authentication.
Resolution
Step 1: Enable PKU2U Authentication
PKU2U (Peer Kerberos User-to-User authentication) is crucial for Windows logins that require online identity support, particularly for Entra ID-joined environments.
A. Registry Update
On the local client machine, we manually created the following registry key:
plaintextCopyEditPath: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\PKU2U
Name: AllowOnlineID
Type: REG_DWORD
Value: 1
📸 Screenshot:
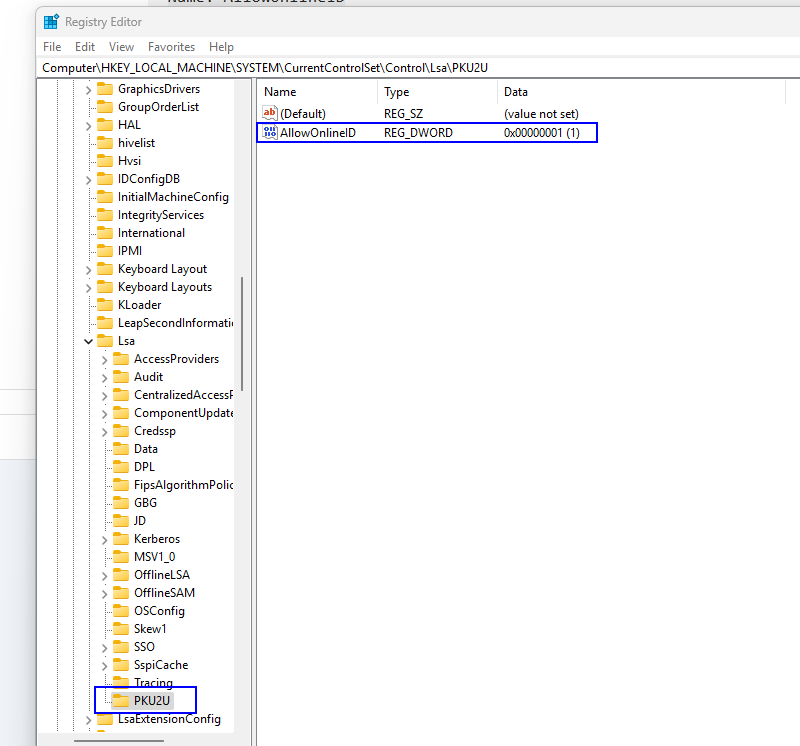
This registry setting explicitly allows the system to authenticate using online identities.
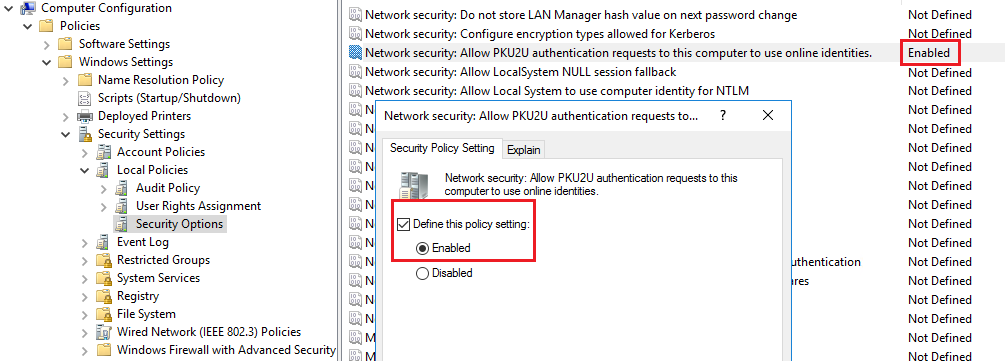
Group Policy Update (for GPO-managed environments)
For machines managed via Group Policy, we also enabled the following:
plaintextCopyEditComputer Configuration >
Policies >
Windows Settings >
Security Settings >
Local Policies >
Security Options >
Network security: Allow PKU2U authentication requests to this computer to use online identities
✅ Set to: Enabled
📸 Screenshot:
Step 2: Disable Per-User MFA
Microsoft Entra ID–joined Cloud PCs do not support per-user MFA. Enabling it can silently block authentication without any error in Azure logs.
To resolve this:
- Disabled per-user MFA for the affected account from Microsoft Entra Admin Center.
- Instead, enforced MFA through a Conditional Access Policy—the supported method for Cloud PC and VM environments.
Best Practices Going Forward
- Use Conditional Access for MFA enforcement in cloud-hosted environments like Azure Virtual Desktop or Cloud PC.
- Ensure PKU2U and online identity authentication is enabled via GPO or registry.
Conclusion
Cloud PCs are powerful—but they rely heavily on proper configuration of both local security policies and Entra ID settings. By enabling PKU2U authentication and moving away from per-user MFA to Conditional Access, organizations can maintain a secure and seamless login experience.
!!! THANKS FOR READING !!!
Regards,
HARISH KUMAR
Knowledge is not a finite resource to hoard; it’s a boundless treasure that grows when shared