MFA was not getting prompted while logging in to RDS and giving error:
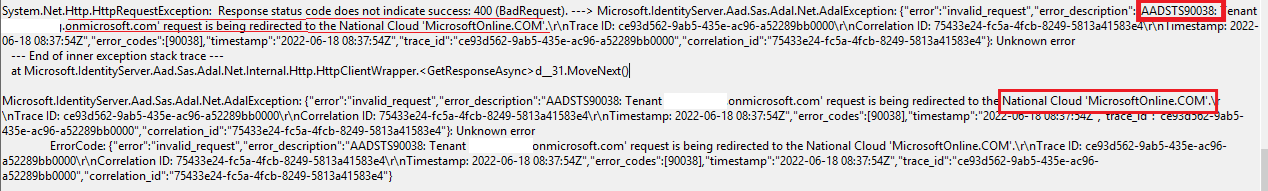
To resolve the above error, followed below steps. Make sure steps required to be performed on all AD FS servers in the farm:
Step 1: Generate a certificate for Azure MFA on each AD FS server using the New-AdfsAzureMfaTenantCertificate cmdlet
The first thing you need to do is generate a certificate for Azure MFA. This can be done using PowerShell.
$certbase64 = New-AdfsAzureMfaTenantCertificate -TenantID <tenantGUID>
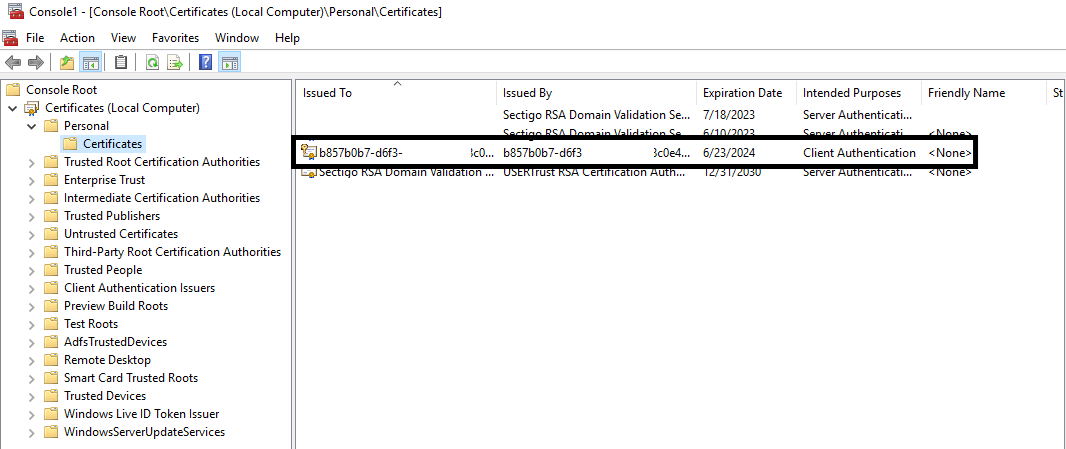
The certificate can be found under certificate console. Go to Run> MMC > Certificates > Personal
For your ref. an example is below:
Tenant GUID can get by going to Azure AD portal > Overview : https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview
Step 2: Add the new credentials to the Azure Multi-Factor Auth. Client Service Principal
To enable the AD FS servers to communicate with the Azure Multi-Factor Auth. Client, you need to add the credentials to the Service Principal for the Azure Multi-Factor Auth Client. The certificates generated using the New-AdfsAzureMFaTenantCertificate cmdlet will serve as these credentials. Do the following using PowerShell to add the new credentials to the Azure Multi-Factor Auth Client Service Principal.
Set the certificate as the new credential against the Azure Multi-Factor Auth. Client
a: Connect-msolservice (Connect to MSOL PowerShell)
b: New-MsolServicePrincipalCredential -AppPrincipalId 981f26a1-7f43-403b-a875-f8b09b8cd720 -Type asymmetric -Usage verify -Value $certBase64
981f26a1-7f43-403b-a875-f8b09b8cd720 is the GUID for Azure Multi-Factor Auth. Client. (This is MFA GUID for everyone globally)
c: Set-AdfsAzureMfaTenant -TenantId <tenant ID> -ClientId 981f26a1-7f43-403b-a875-f8b09b8cd720
d: Open Registry Editor on the AD FS server.
e: Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ADFS. Create the following registry key values:
NOTE: Above URL’s give are for Government tenant as it all ends with .US, if you are from commercial then use .COM apart of .US
Restart the AD FS service on each server in the farm before these changes take effect.
Go to run> PowerShell > Restart-service adfssvc
After this, you will see that Azure MFA is available as a primary authentication method for intranet and extranet use. To check Go to> ADFS > Server manager > Tools > ADFS management >
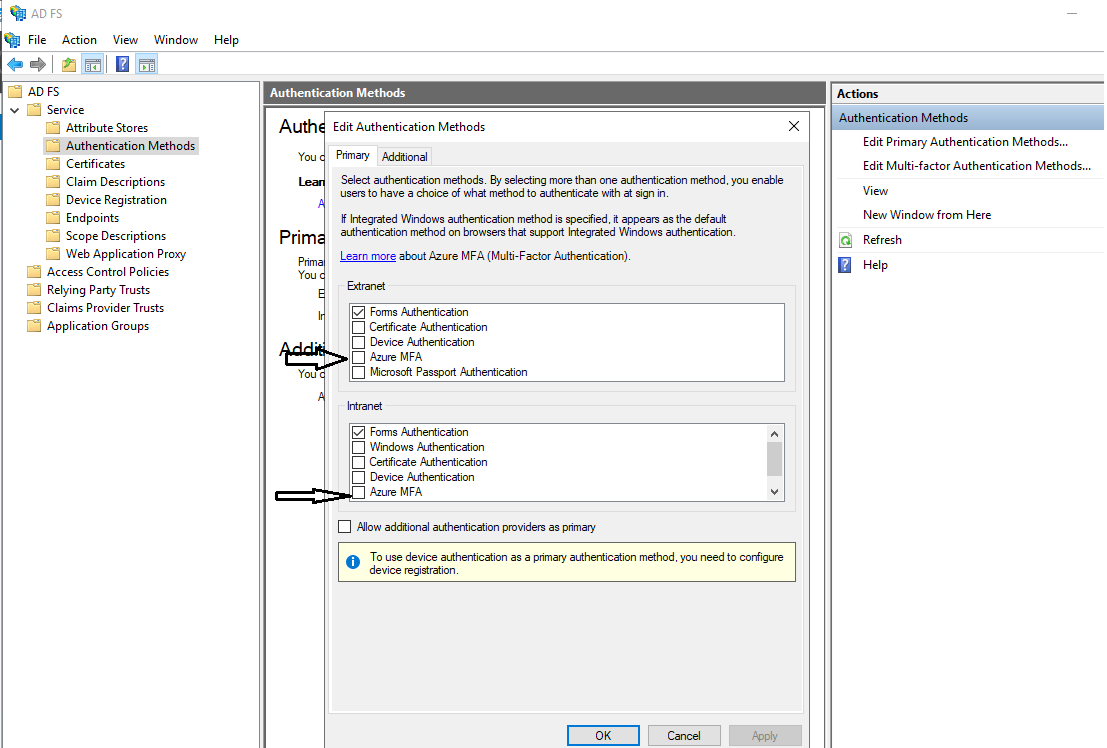
NOTE: While creating the Relying Party Trust you need to select as Claim Aware and configure it further.